Knowing an information system’s vulnerabilities is necessary but not sufficient. For effective protection, organisations need a complete view of the risk situation: vulnerabilities, measures, threats, impacts. This complete vision is provided by risk analysis and security assessment methods. The global methodological benchmark in this field revolves around the ISO 2700x standards: ISO 27001, ISO 27002 and ISO 27005.
EGERIE deploys a variety of standardised risk analysis methods, which are described below.
EGERIE supports the deployment of an ISO 27001 approach through its Risk Manager solution.
The ISO 27001 standard describes the development of an ISMS (Information Security Management System) as a process, in the same way as the ISO 9001 standard describes the quality process. Like ISO 9001, ISO 27001 is based on the widely used Plan-Do-Check-Act (PDCA) model. This model incorporates the fact that security is an iterative process consisting of the preparation and planning of the ISMS in sequence. ISO 27001 also reflects the principles of the OECD guidelines on the security of information systems and networks. ISO 27001 certification demonstrates that the ISMS fulfils the company’s security needs. The certification is performed by an accredited auditor. On the basis of the ISMS, the auditor verifies that the selection of countermeasures is appropriate and has been documented following a formal risk analysis, and that the countermeasures have been implemented correctly and in full. The auditor is responsible for judging whether the standard has been properly applied and the countermeasures are sound.
The ISO 27005 standard describes the outlines of risk management from the viewpoint of implementing an information security management system. Aligned with the ISO 27001 and ISO 27002 standards, and using the vocabulary defined in ISO 27000, the ISO 27005 standard is the benchmark for conducting a cyber risk analysis and setting up a risk management process based on a management system incorporating the PDCA (Plan, Do, Check, Act) continuous improvement approach:
Complementing the ISO 27005 standard, ISO 27002 supplies a series of best practice recommendations for security. These “Business Best Practices” enable companies to respond quickly and effectively to any circumstance without having to reinvent security principles and technical solutions from scratch.
EBIOS Risk Manager is the new digital risk assessment and treatment method published by the French national information system security agency (ANSSI) with the support of Club EBIOS.
EBIOS Risk Manager makes it possible to identify and evaluate risks, and determine security measures to deal with them. It also enables users to approve accepted risk levels and adopt a long-term continuous improvement approach. Lastly, it provides the required features for communication and decision-making within the organisation and with partners.

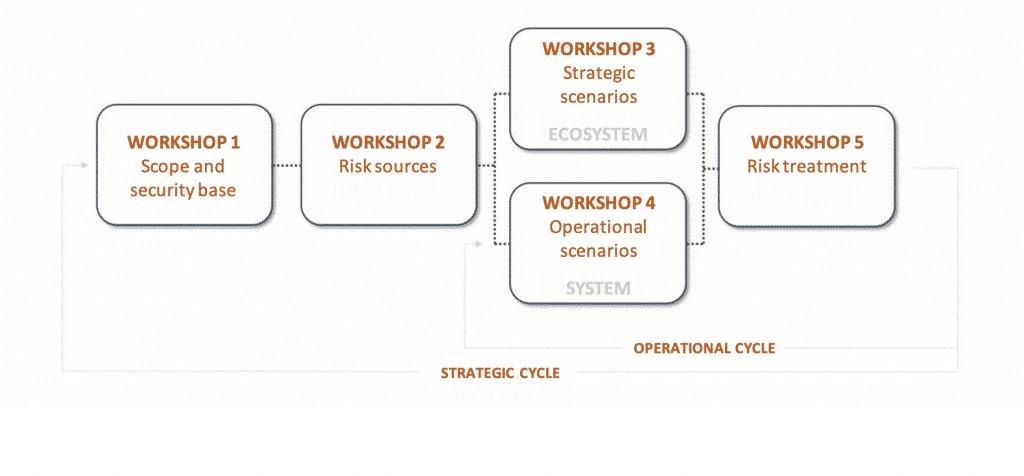
The EGERIE Risk Manager software is compatible with all versions of the EBIOS method (V2, 2010 and the future version under development). The EBIOS method (Expression des Besoins et Identification des Objectifs de Sécurité – expression of needs and identification of security objectives) is used to evaluate and address risks relating to IT system security. It can also be used to communicate about these risks within the organisation and with partners as part of the IT security risk management process. Created by ANSSI in 1995 and updated regularly, the EBIOS method builds on 15 years of experience in the field of risk management.
MEHARI, published by CLUSIF, is a risk analysis method that covers both the organisational and the technical aspects of IT security. MEHARI provides the framework for a security audit leading to an assessment of risk levels in a series of areas: general organisation, physical security, logical security, application security etc. This assessment can then be used to select security measures to plug the gaps as effectively as possible, bringing the degree of risk in each area to an acceptable standardised level.
CRAMM is a risk management method used by the British government. It is large and comprehensive (over 3,000 checkpoints) and thus once again suited only to large organisations (it has 550 customers worldwide). Following the creation of the 2002 version of BS 7799-2, Siemens (formerly Insight Consulting) created a new version (CRAMM version 5.0), which targets BS 7799 certification.
EGERIE enables industrial companies and defence authorities to prepare the documents essential for security approval processes.
The Network and Information Security (NIS) directive aims to ensure a shared high level of security for networks and information systems in the European Union. It was adopted on 6 July 2016. It aims to achieve the implementation of effective European cooperation and the protection of critical economic and societal activities as a collective response to the risk of cyberattacks.
The General Data Protection Regulation (GDPR) is a European regulatory text that provides a framework for processing data fairly across the whole European Union. It took force on 25 May 2018. The GDPR builds on the French data protection act of 1978, which sets rules on the collection and use of data in France. It was designed to achieve three goals: